Types of Cyber Threats
Some common types of cyber threats are described below.

Introduction:
Many businesses in this modern era use computers to maintain track of their data and run their operations. What will you do if your computer contains critical data from your company and is stolen by your competitors? A cyber security threat is defined as unauthorized access to your data or any destructive assault that aims to acquire unauthorized permissions, disrupt digital activity, or destroy information.
What are the Cyberthreats?
A cyber security threat or cyber threat is a malicious poisonous act that has the motive to steal or damage the data from the digital wellbeing and stability of an enterprise. There is a wide range of cyber threats which include computer viruses, denial of services, and many other numerous vectors.
What is the aim of cyber threats?
The purpose of cyber threats is to steal, disrupts, gain the sensitive information of an organization, unauthorized access to the data of an organization, and damage an IT asset, computer network, and intellectual property. Threats might occur from trusted internal users as well as unknown external parties in faraway regions.

What are the types of cyber threats?
Cybercrime:
Covers individuals or organizations that attack systems for monetary gain or to wreak havoc.
Cyber-attack:
The collecting of information is frequently motivated by political considerations.
Cyber terrorism:
Cyber terrorism is designed to generate panic or anxiety by undermining electronic systems.
What are some common methods used to threaten cyber-security?
Malware:
- Virus:
A computer virus is an application that is installed in your computer without the knowledge of the user and it is harmful and damaging software and comportments malicious acts.
- Spyware:
An application that secretly records the whole thing an operator implements in order for hackers to profit from it. Spyware, for example, may your credit card information be recorded.
- Ransomware:
Ransomware is a kind of malware that practices encryption to retain a victim's data hostage. The vital data of an individual or organization is encrypted, building it impossible for them to access files, folders, databases, or apps. Then a ransom is asked in order to get access.
- Adware:
Adware is software that may seem on your mobile device or computer and show unwelcome pop-up advertisements or billboards. Instead, there may be damage or shortcoming in your comport of an operating system or software that hackers can practice to penetrate your device with malware, counting some forms of adware.
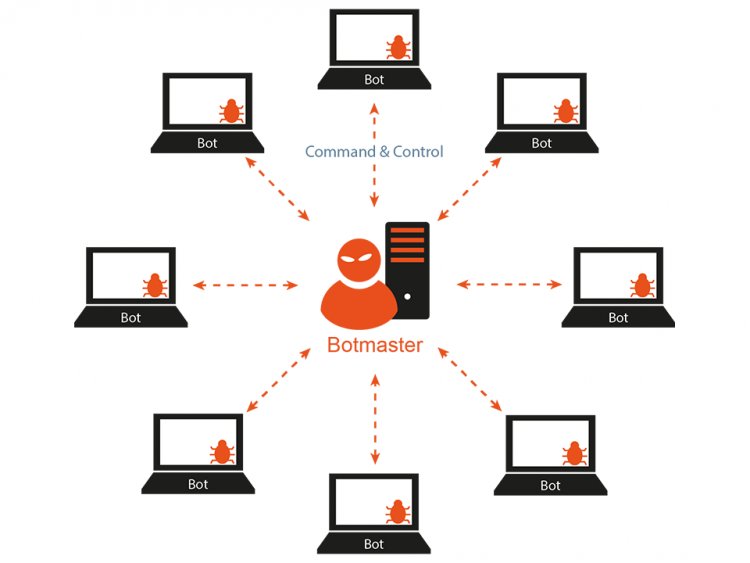
- Botnets:
A botnet is a pool or group of malware-infected PCs well-ordered by a solitary attacker or mugger known as the "bot-herder." A bot is a solitary machine that is below the controller of the bot-herder. They're also used to circulate bots so that the botnet may recruit additional technologies.[1]
What are the tips for cyber safety?
How can people or organizations shelter and safeguard themselves against cyber threats? Here are specific of our greatest cyber-security commendations:
- Update your PCs and operating system:
By updating your software on a regular basis warrant that you have installed the utmost up-to-date security updates.
- Install anti-virus software:
Anti-virus software, for example, Kaspersky Total Security, will identify and disregard fears. For the uppermost level of security, you need to keep your software up to date.
- Use heavy-duty passwords:
Make sure your passcodes are difficult that if anyone wants to access your computer the difficult passwords are not easy to guess.
- Do not open attachments from unknown sources in an email:
There's a chance they're infected with malware.
- Do not click on links in emails from unknown sources or strange websites:
Malware is occasionally broadcasted or spread by connecting on links in emails from strange dispatchers or unaccustomed websites.
- Avoid utilizing public Wi-Fi networks that aren't secure:
You're unprotected from man-in-the-middle occurrences if your network is not secure.
Conclusion:
Cyber security refers to the collection of methodologies, technologies, and procedures used to safeguard the confidentiality, integrity, and availability of computer systems, networks, and data against cyber-attacks or unauthorized access. One of the most crucial parts of the fast-paced, ever-changing digital world is cyber security. Its threats are difficult to dismiss, therefore learning how to guard against them and teaching others how to do so is critical.
- What is Cyber Security? ; Available from: https://www.kaspersky.com/resource-center/definitions/what-is-cyber-security.

 admin
admin