This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
Cloud Computing
Information Security
Information security helps to keep the data safe from unauthorized access.
Application Security
Application security is the process of making apps more secure by finding, fixing,...
Network Infrastructure Security
Network Infrastructure Security means protecting your network from unauthorized...
Services of Cloud Computing
Well, there are 3 types of cloud computing services: Infrastructure as a Service...
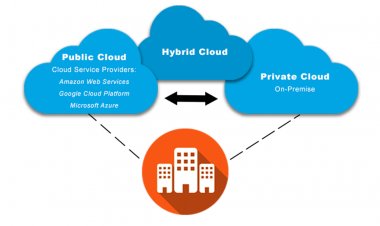
Types Of Cloud Computing
There are 4 main types of cloud computing: private cloud computing, public cloud...
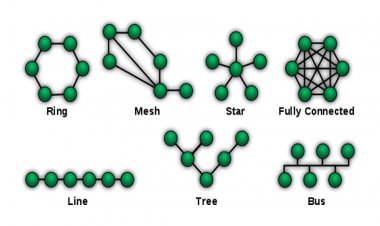
Network Topology
The Network Topology refers to stations connected to a network connection. There...
Internet of Things
Internet of Things (IoT) turns inanimate objects into intelligent ones by linking...
Bulk IP changing from DNS after server migration VestaCP
Here I create a Bash script for VestaCP to automatic IP update in all over the domains...
Cloud Computing
The supply of computer services is called cloud computing. Cloud environment gives...
Cyber Security
Cyber security is a technological application that uses process and control to protect...